In order to improve the security of our critical resources and data, Information Services will be making a series of changes to our Duo 2FA service over the next several weeks. These changes may impact you. Please review this list of changes to understand these impacts and your options.
Jump to February 27 changes: Verified Duo Push
Jump to February 29 changes: Expanding to Additional Apps
Jump to March 12 changes: New device alerts and out-of-date device warnings
Changes to Duo starting Tuesday February 27th:
- Verified Duo Push will be enabled Duo "Verified Push" prompts you to enter three to six digits during the Duo MFA sign-in process if a risk has been identified during authentication. More about Duo Verified Push on Duo's website
With Verified Duo Push, authentication happens normally unless Duo determines an authentication attempt is unusual or higher risk through a combination of factors:
- Login location "Impossible Travel" - (i.e., login from Santa Clara & Japan in the same hour)
- User denying authentication repeatedly or reporting fraud
- Login from a new, unremembered device in combination with other factors
- Login to multiple user accounts from the same session
What does this look like?
If Duo detects a high-risk condition, the authentication will require a stronger second factor (typically a Verified Push) where you will need to enter the 4-digit number from the webpage into your Duo Mobile application.
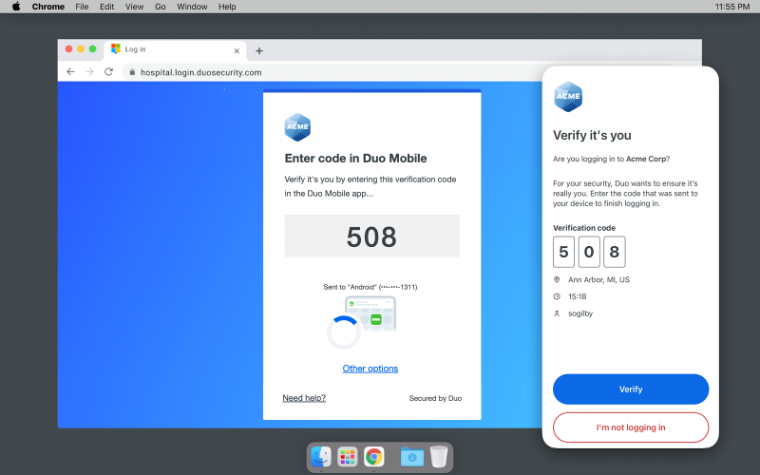
Note: If you receive a Duo prompt during a time you are not logging into an SCU application, it is important that you deny the request and immediately alert the Information Security Office at iso@scu.edu so we can secure your account.
Expanding Duo Apps Thursday Feb. 29th
Duo will be enabled for a handful of additional applications that previously did not require 2FA. These include Terminal4, Room Reservations, Phonebook, Evaluations, and other SCU custom apps. No action is required on your part.
Changes to Duo starting Tuesday March 12th:
- New device alerts will be enabledFaculty, Staff, and Students will be alerted by email when a new authentication device (such as a smartphone or a Security Key) is enrolled in your Duo account. Note: If you receive this email alert and you did not enroll a device, it is critical that you immediately contact the Information Security Office at iso@scu.edu so we can secure your account.
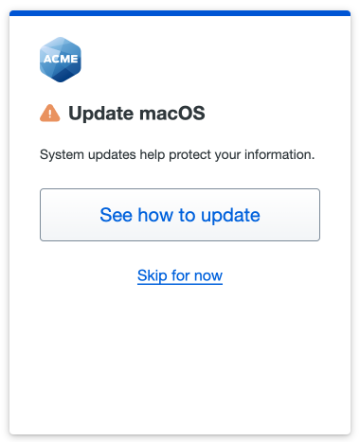
- Out-of-date device warnings will be enabled Faculty, Staff, and Students who use out-of-date devices (devices with older/unpatched operating systems or browsers) will begin receiving warnings when they authenticate to Duo. Your access will not be blocked, and you can proceed by clicking the “Skip for now” link on the dialogue box. However, we recommend you update your device as soon as possible.
Changes to Duo starting Tuesday March 26:
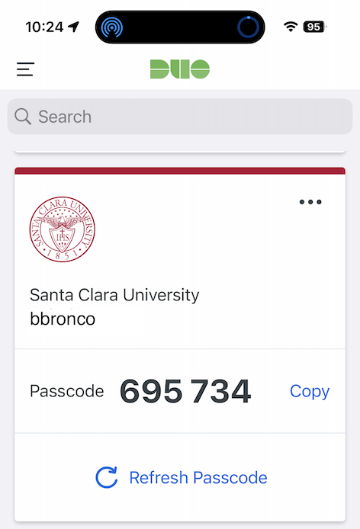
- Duo mobile app passcode option will be eliminatedIf you do not use the Duo mobile app passcode feature, you can ignore this change. For smartphone users with the Duo Mobile app installed, you will no longer be able to use the app passcode feature (pictured below) with SCU’s Duo Service. If you use the mobile app passcode feature, you must move to an alternative method, such as Push, Security Keys, or our Bypass Code Generator. Faculty and Staff can receive a free USB Security Key at the Technology Help Desk.
- For faculty and staff only, smartphone screen locks (PIN) and encryption required, “jailbroken” devices prohibited
Students will not be impacted by this change.Smartphones lacking screen locks and encryption are unsafe to use and must not be used to access SCU secure resources and data. If this change affects you, you can enable a screen lock on your smartphone (which will typically also enable encryption) or switch to another authentication method to access Duo protected resources, such as a Security Key or the Bypass Code Generator. Jailbroken devices (which are devices where the operating system has been permanently tampered with) cannot be configured to work with Duo. If you have a jailbroken device, you must switch to an alternative authentication method or smartphone.